NEWS 》 Weekly News Digest - Week 8 - February 2018
Asymmetric Processor Cores
Most Intel processors use one of two cores, the main-line core and the Atom core. Desktop processors might use the newer Kaby Lake or Coffee Lake micro-architecture cores,
while the Xeon SP lines uses the previous generation Skylake micro-architecture. All of these are part of the main core line. The Atom core is used in Xeon Phi,
Atom and some Pentium or Celeron processors. In simple terms, the main-line is a big core and the Atom is a small core...
Read More



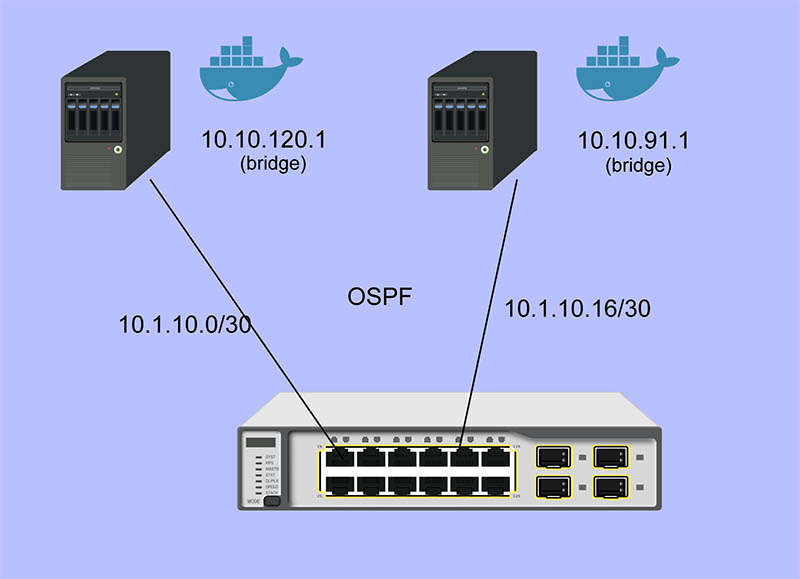
Using QCT Quanta LB6M 10GbE Switch for Container Networking
Quanta LB6M is everywhere, yet you won’t find it on Quanta’s website. That’s because it’s not sold to end users,
it is an early hyper-scale switch based on the Scorpion chipset. It’s the first 10 GBit/s merchant silicon chipset
used by Google and probably others in the development of their large-scale networks...
Read More
Using SSE Instead Of WebSockets For Unidirectional Data Flow Over HTTP/2
When building a web application, one must consider what kind of delivery mechanism they are going to use...
Read More
Why IPv6 networks create DNS configuration problems
DNS data is among the most basic and crucial information required for network connectivity, but configuring DNS recursive servers in IPv6-only networks can pose challenges...
Read More
Hypervisor or containers: Which solution is right for you?
There are a lot of considerations to make when using virtualization technologies. Finding a solution which balances performance and security can be challenging...
Read More

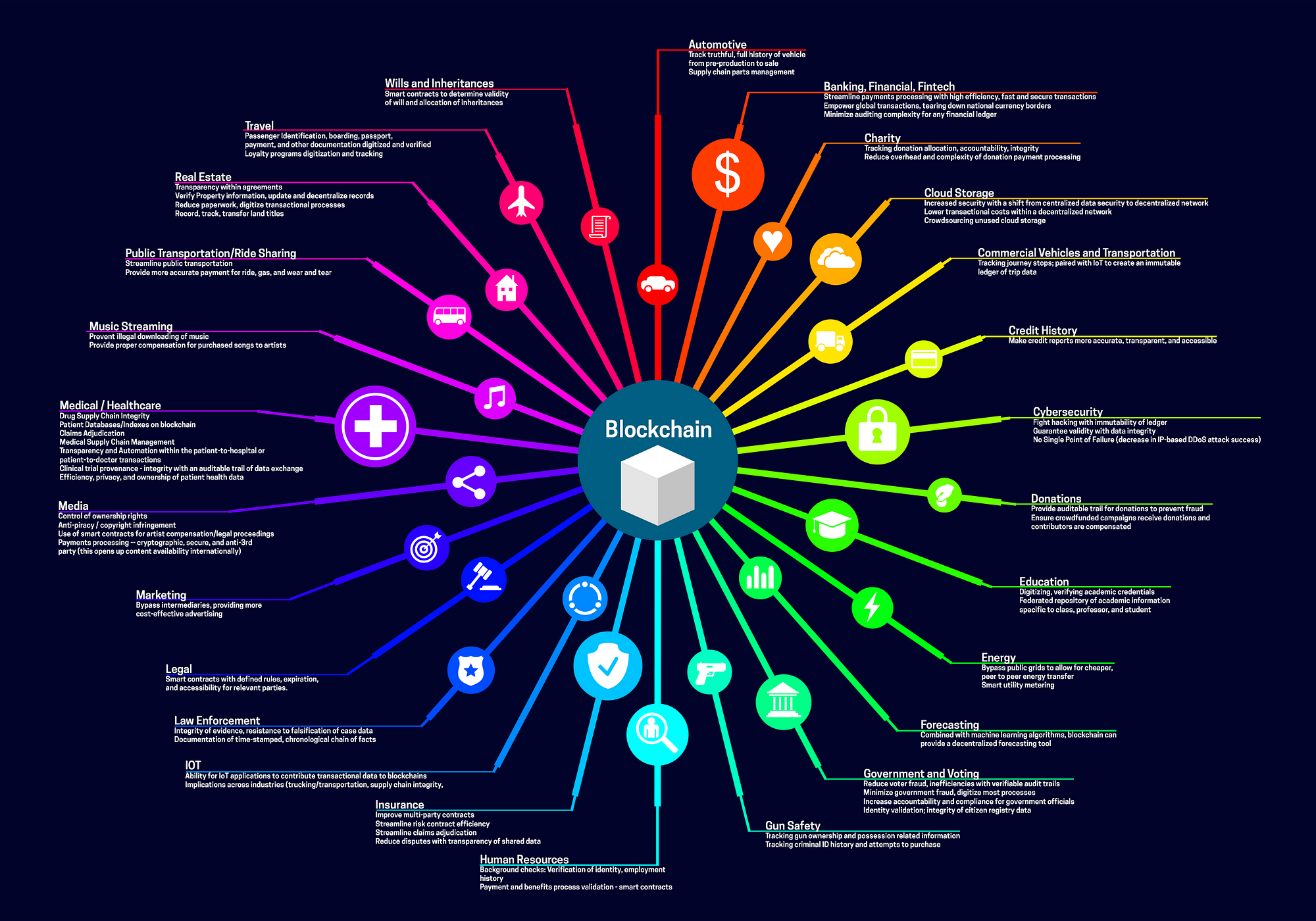
Blockchain for 2018 and Beyond: A (growing) list of blockchain use cases
The blockchain process of transacting and storing information on a decentralized, distributed ledger yields many benefits for enterprise application data...
Read More
Raw sockets backdoor gives attackers complete control of some Linux servers
A stealthy backdoor undetected by antimalware providers is giving unknown attackers complete control over at least 100 Linux servers that appear to be used in business production environments, warn researchers...
Read More

Suggested Topics:
Join The Linux Channel :: Facebook Group ↗
Visit The Linux Channel :: on Youtube ↗
💗 Help shape the future: Sponsor/Donate
Recommended Topics:
Featured Video:
Trending Video:
Saturday' 13-Mar-2021
Recommended Video:









